IoT
5-Minutes Guide to Securing and Managing Your IoT Devices
 Updated 12 Jun 2024
Updated 12 Jun 2024

Transform your business landscape with the power of the Internet of Things (IoT). At Q3 Technologies, we specialize in delivering cutting-edge IoT app development services designed to enable seamless connectivity and smart solutions. As a leading IoT development company, we are committed to driving efficiency and fostering innovation. Starting with ransomware and ending with distributed denial of service (DDoS) attacks and the inclusion of legacy devices, it seems that IIoT threats do not know their limits. The increase in the use of IIoT and the creation of new threats means that organizations in the critical infrastructure sector must step up their security measures. Whereas 96 percent of the business leaders recognized that their organization was required to step up the investment in industrial security, 93 percent of organizations have been at a failure level in their IIoT/OT security projects. This is often due to a lack of understanding of IIoT security, the challenges typical to it, and ways of overcoming those challenges. IoT Device Security demands total visibility of your assets and how they are connected. However, growing networks, an intricate web of connections, and the reliance on traditional systems make it almost impossible for corporate entities to start the transition process.
What is IIoT Security?
IIoT, or Industrial Internet of Things, refers to the actual use of sensors, instruments, and other connected devices, which are linked through the Internet to improve industrial and production processes and solutions. As a crucial aspect of IoT app development services, IIoT focuses on the enhancement of efficiency, promoting the interaction between machines, and the automation of processes in industrial contexts. At Q3 Technologies, a leading IoT development company, we harness the power of IIoT to drive innovation and optimize operations across various industries.
While peripheral connected IIoT systems and devices have improved the aspect of industrial automation, they also pose a number of challenges to CISOs and their security squads. While designing IoT devices and their operating systems, security is hardly given any consideration. They may have operational lifespans of up to decades – thus making them susceptible to cyber threats such as DoS, malware and ransomware, phishing, as well as social engineering and supply chain threats.
Businesses need to always be ahead in their fight against hacker and other forms of digital threats in their industrial systems and devices. Enter IIoT security. IIoT security is crucial as it offers protection to sensitive systems like manufacturing facilities, power supply chains, transportation systems, healthcare equipment, and other industrial settings from cyber risks and breaches.
IIoT security defines how companies protect their Internet of Things solutions, including devices, connections, information, and networks in industrial settings. Since the IIoT is applied in critical processes and operations in industries, the effect of security threats can be severe or even dangerous outcomes (for instance, a virus attacking healthcare equipment).
Furthermore, downtimes of the IIoT devices can cause some minor inadequacies and emergencies. Therefore, securing IIoT systems is critical in order to protect industrial processes and systems, increase safety, and prevent or mitigate cyber attacks.
Read Our Case Study: IoT-Enabled Transformer Monitoring For A Leading Energy Resource Company
Importance of IIoT Device Security
Since IIoT security keeps everything in industries operating efficiently and safely, it is essential. It’s similar to having a guard for your important belongings. Why it matters is as follows:
- Machine Protection: IIoT security ensures that industrial and manufacturing machinery are secure from cyberattacks. This indicates that there are no interruptions to their job.
- Data Protection: It also ensures the security of critical data. IIoT security prevents the possibility of someone stealing proprietary ideas from your industry.
- Accident Prevention: IIoT security helps avert mishaps by monitoring machinery. If a machine is about to perform a risky task, it can be stopped.
- Keeping Costs Down: Businesses don’t have to spend a lot of money resolving issues brought on by accidents or hackers when everything is secure.
- Increasing Efficiency: IIoT security makes machines function more effectively, which leads to the production of better and faster goods.
To put it simply, IIoT security is an industry equivalent of a superhero. Managing IoT devices ensures that everything operates smoothly, safely, and without any expensive disruptions by protecting computers, data, and people.
Why Are IoT Devices So Difficult to Secure?
From a statistical perspective, each new device is a potential vulnerability, the chance of which can be exploited by an attacker. Malware may take advantage of vulnerabilities that exist in embedded software on endpoint devices. They can then be leveraged as part of an attack chain to guide threat actors further into more sensitive areas of the IT infrastructure. On the other hand, these devices can be used as bots to launch the so-called denial-of-service attacks. Unfortunately, most security products only support a percentage of such devices or need an agent to be installed for monitoring. Most of the IoT, including the premium devices, remain unmonitored.
The Challenges of Securing IIoT Devices
IIoT security can be difficult for industrial companies because of the nature of IIoT devices and systems, as well as the factors involved when making them a part of the system.
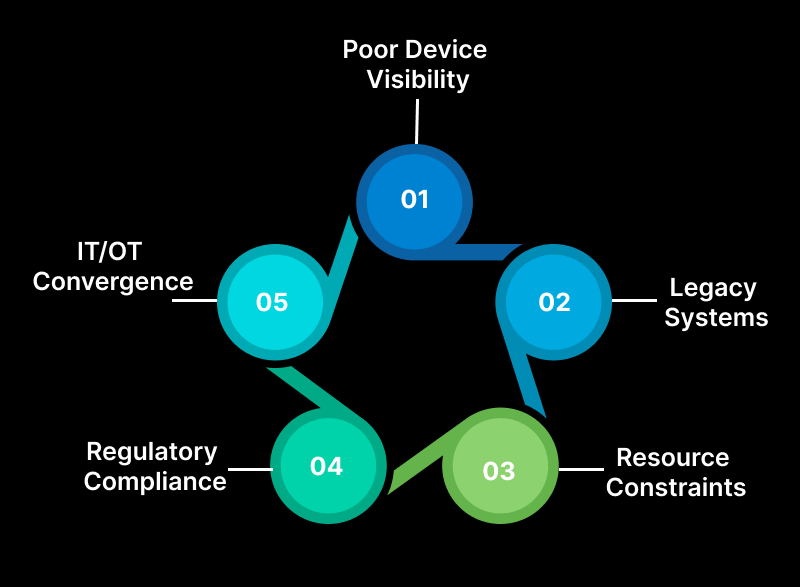
1. Poor Device Visibility
IIoT environments typically include a diverse range of devices made by several manufacturers, each with its own set of standards and protocols. Because of this, it is challenging for enterprises to know exactly which devices are present in their environment and to have total visibility.
2. Legacy Systems
Most of the industrial devices and systems are old, dating back to the 70s and 80s, and were originally designed to function and be robust but not secure. These systems are inherently non-IoT compliant because they were not designed or developed to connect to the Internet. The lack of security features like encryption, authentication mechanisms, or communication protocols makes them vulnerable to attacks. Also, the older software is vulnerable to known vulnerabilities that hackers can take advantage of.
3. IT/OT Convergence
IT networks, which were not intended to be linked and managed in the same manner, are beginning to converge with operational technology (OT), which was traditionally “air-gapped.” The increased attack vector that cybercriminals can now take advantage of is the result of this convergence.
It has also led to complexities in establishing a coherent IAM framework, as groups require synchronizing different user access needs, user roles, and authentication types between IT and OT domains. Such gaps could be closed with effective identity governance frameworks in place.
4. Regulatory Compliance
The critical infrastructure sectors may also implement frameworks such as NIST to protect their assets better or demonstrate improved compliance with regulations. Thus, although there are set frameworks that assist with regulation, the rules are complicated and constantly evolving, making them difficult to deal with.
Special regulatory requirements, depending on the type of your organization’s activity, can be NERC-CIP, TSA, HIPAA, or ISO/IEC 27001. This makes IIoT security a little bit more challenging since compliance failure elevates cyber risk and may lead to lawsuits or legal repercussions.
5. Resource Constraints
Most of the industrial organizations may not have enough qualified personnel who would have undergone training in IIoT cybersecurity and may also have limited funding. Consequently, they are inclined to focus on other operational requirements instead of protective measures against cyber threats.
Redressing the scarcity of resources in IIoT settings can be informed by target asset categorization that results from risk evaluation. Businesses should also enhance their hardware, boost software performance, and develop cost-efficient protection measures in relation to their issues.
IoT Security Guide to Protect IoT Devices and OS
Solving the challenges mentioned above calls for an integrated approach that encompasses the application of cybersecurity measures, legal requirements, best practices, and constant training and sensitization on cybersecurity. Nevertheless, your organization may encounter challenges in determining the starting point. Here are five basic steps to help you begin to manage IoT devices.
1. Maintain an up-to-date Asset Inventory
First and foremost, one must take stock of existing assets. In order to make the decisions concerning the security of the IIoT, you need to know what devices are connected to your sensitive environment.
An industrial cybersecurity solution can thus provide an updated and accurate evaluation of your assets. There are a number of tools available that have multiple and highly flexible discovery methods with which you can effectively mix and match. These inventories provide full transparency of your IIoT environment, allowing you to have device control and develop risk and vulnerability management strategies.
2. Apply Network Segmentation
Network administrators can regulate the traffic flow of the subnet by partitioning the networks into segments or zones depending on granular network policies. Network segmentation in organizations can lead to increased security as well as increased efficiency and productivity. This architectural approach is relevant to IIoT settings because they manage and oversee essential infrastructures and devices that govern physical procedures.
With edge computing, you can place computing resources closer to the network edge and allow localized data processing and traffic distribution. Moreover, simplified communication protocols may limit the amount of information that requires transmission and enhance the process of communication between the connected devices and systems to make a network less complicated.
3. Implement Secure Access
Unfortunately, many IIoT systems do not have adequate protection measures, especially with regard to access control. This makes it easier for hackers to infiltrate and manipulate key systems. If access is not secure, organizations will not be able to monitor or control what happens within their environments adequately, which affects uptime and safety.
Therefore, there is a need for an industrial solution for remote access that lowers your mean time to repair (MTTR), decreases the cost and effort of setup and management of remote access for the personnel, and lessens your IIoT system vulnerability to threats from unmonitored, unconstrained, and insecure connections.
4. Establish Exposure Management Strategies
Most of the IIoT devices were not designed with security in mind, and they are, therefore, at high risk of cyber threats such as DoS, phishing, and device hijacking. However, the bitter truth is that the standards and tools that are being employed by security operations teams are not optimized for the task.
Evaluating exposure is a process that allows you to decide which vulnerabilities in your environment should be remediated first. This customization will assist you in comprehending how the particular classes and instances of vulnerabilities are threats to your organization and how best to protect yourself.
5. Continuously Monitor for Threats
Industry environments bear no exception to threats, and that is why it is important to identify them when they present themselves. One way to improve their cybersecurity posture would be through continuous monitoring and detection of policies and procedures. This ongoing monitoring will enable you to prevent, identify, and mitigate cybersecurity threats and incidences that may impact significant operations.
Secure Your IoT Devices and OS with Q3 Technologies
With the continued integration of new technology into their essential industrial processes and complex environments, there is an increased vulnerability that necessitates the protection of essential IIoT systems.
Before sketching out the plan for implementing IIoT security, they must identify the essential resources in the environment. As for the remaining points, you can follow them to promote an effective strategy from there.
To implement these measures rapidly, your organizations should collaborate with an industrial cybersecurity provider such as Q3 Technologies to obtain IIoT security targeted at your firm.
Our team at Q3 Technologies has direct experience with the path and obstacles involved in achieving cyber resilience throughout the IIoT cybersecurity maturity model. Connect with our talented team to get a customized IoT security guide.
FAQ
Q. What is the Industrial Internet of Things (IIoT)?
A. IIoT is an industrial network of devices that is used to improve manufacturing and industrial operations and convey data.
Q. What is the Difference Between IoT and IIoT?
A. Scale differences are the primary difference between IIoT and IoT. Consumer electronics like smart thermostats and fitness trackers are typically referred to as being part of the Internet of Things. The term “industrial Internet of Things” (IIoT) describes devices that power businesses on a much bigger scale. One example of this is supply chain management equipment.
Industrial IoT is a word specifically designed to focus on more intricate networks of devices meant to drive production, but IoT can be used as a general term to encompass all internet-enabled devices.
Q. What Role Does IIoT Play In Factories?
A. IIoT is utilized in manufacturing to optimize output and boost efficiencies. To complement their operational technology goals, OEMs are producing an increasing number of embedded devices with IT features. Manufacturers establish what many refer to as “smart factories” by gathering and evaluating data from these devices in real time.
IIoT has drastically changed production in this way. The integration of IIoT devices has the potential to streamline an industry that was previously highly fragmented. Let’s examine the ways that IIoT improves production efficiencies.